本研究旨在探讨云测试的安全问题。虽然越来越多的企业开始向云环境迈进并共享信息,但他们同样十分关注云环境的安全问题和可能存在的风险。综述测试过程中安全保障方法的现有概念,在此基础上重点归纳和分析公共云测试中的信任、治理、承诺、认证与访问管理、可用性、数据安全、隔离及失败、架构这8类安全问题的风险程度,并对典型的公共云服务提供商在这8类安全问题上所采取的安全策略进行实证分析。
The objective of this study is to evaluate security issues of cloud testing. Organizations are increasingly moving to the cloud and sharing their information, but there are concerns about security issues and risks that may arise due to security breaches. This paper extends the concept of security approach during testing. It makes use of a literature review to evaluate the risk of eight security issues when testing in public clouds. The security issues including trust, governance, compliance, identity and access management, availability, data security, instance isolation and its failures, and architecture in testing on a public cloud. The paper also includes an empirical survey to evaluate the current security strategies of different public cloud providers on the eight security issues.
Cloud computing and cloud testing offer a new delivery model of services. Cloud delivery models affect the acquisition, business, access and technical models of testing. It emphasizes pay per use pricing models instead of license fees. Cloud computing creates a new era on both aspects of technology and finance from installing software to using hardware. A Gartner report defines cloud computing as “a style of computing where massively scalable IT-enabled capabilities are delivered ‘as a service’ to external customers using Internet technologies”[ 1]. The numerous features of cloud computing along with the different types of deployment models i.e. public, private, hybrid and community clouds have opened a new arena of possibilities and opportunities for testing. Testing of an application has traditionally been viewed as an integral and necessary, but unpleasant factor because it requires large infrastructure and lots of resources. Moreover, the business and real-time environment applications are used increasingly, but their complexity makes it more difficult for an organization to build and maintain their testing environment. At the same time, testing, especially when performed in public clouds presents a new set of challenges and risks like privacy, data integrity, lack of control, availability, manageability, business acceptability and security[ 2].
According to the 2008 International Data Corporation (IDC)’s Information Technology (IT) Cloud Services User Survey, 74.6% of IT executives and Chief Information Officers (CIOs) cited security as the top most challenge preventing their adoption of the cloud services model[ 3]. Even though organizations are getting benefits from the security and privacy policies of public clouds, there are considerable amounts of security flaws in the aspect of risk and threats. Risks include, for example, unauthorized access to the data, Structure Query Language (SQL) injection, account or service hijacking, cross-site scripting, malicious insiders and data loss or leakage, as all the data and content will be publicly available. Hence, it is very essential to be conscious of the security aspects while testing applications in public clouds.
Cloud computing environments can be divided into four service layers: Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS) and Human as a Service (HuaaS) which present and contain different levels of responsibility for security management. Security issues and risks posed by public clouds should always be taken into consideration before moving the business applications to the public clouds. In fact, the cloud does not increase the risk but it is inevitable that if subscribers neglect the security aspects, then the security risk would increase[ 4]. The cloud provider itself cannot assure complete security for the subscribers because some security risks are introduced by the subscribers own applications and data. However, there is still no appropriate and systematic testing approach addressing security especially in risk-based security testing in public cloud environments. Therefore, it be right to say that the approach and the procedure for recognizing risks basically depend upon the level of understanding between cloud providers and subscribers.
The objective of this study twofold:
(1)We use a literature review to evaluate the risks and threats associated with various security issues when testing public cloud applications.
(2)We use an empirical survey to understand the existing security strategies employed by different cloud providers.
Initially, cloud testing was related to load and performance testing of websites and their applications[ 5]. Increasing demand, requirements and maturity of technology made cloud testing more realistic for testing of all kinds of enterprise software for functional and non-functional issues before deployment[ 6]. Cloud testing is a form of software testing in the cloud that uses cloud computing environments and lies at the intersection of software testing, systems integration and cloud computing[ 7]. It helps organizations that are pursuing load and performance testing and service monitoring to ensure the quality of the service. Enterprises are realizing the importance of cloud testing and they are taking the cloud route for the potential benefits to their organizations.
Traditional software testing procedures are often inadequate due to limited computing power, performance and capacity of enterprise’s infrastructure. Approximately,﹩3 million investment is required to test an Internet-scale application deployment[ 8]. This is not considered as feasible, economical and practical in small and medium scale business enterprises. Cloud testing provides similar opportunities for testing as traditional software testing with just a fraction of the cost because of the pay per use pricing model. However, there are plenty of challenges that have to be addressed by the cloud service providers as well as the subscribers. The key aspects which are critical during cloud testing include[ 9]:
Multi-tenancy refers to a process of sharing resources to run an instance of software to serve multiple clients. The different types of deployment models place heterogeneous roles and requirements in multi-tenancy. It is regarded as an essential attribute of cloud computing and it is important to understand the degree of multi-tenancy. Testing of multi-tenancy during the initial phase is one of the challenges in cloud testing since the same data instance has to behave differently for different clients[ 9].
Service Level Agreement (SLA) Governance is also a key challenge in cloud testing. The service level agreement should be done between the customer and the cloud service provider before testing. It is also important to follow the initial recommendation that has been setup by the computing standards such as National Institute of Standard and Technology (NIST)[ 10].
Security is one of the prime challenges of cloud testing. It is one of the major reasons why organizations step back from the adoption of cloud testing. There are few guarantees about the security and service quality in public clouds. Therefore, subscribers should understand the risk posed by public clouds and they should establish the level of trust with cloud providers.
After security, subscribers as well as service providers take data integrity and privacy as the critical challenges during cloud testing. The applications deployed to cloud are not always designed with data integrity and privacy. This problem may lead to the deployment of vulnerable applications into cloud with security issues[ 11].
License commitment and its access are the integral steps that different organizations have to face during the use of test tools. Different types of license models have to be verified during testing[ 12]. Therefore license management is an important parameter to be observed.
The other basic challenges of cloud testing include, for example, regression testing, maintainability testing, release management, compliance with standard regulatory and integration of on/off premises systems[ 13].
The organizations can achieve maximum output of their cloud testing by following cloud based test strategy. It is important to initiate and document the test strategy before starting the cloud testing. The document may include testing goals, identifying the various types of testing to be performed, benchmarks, selection of cloud test environment and infrastructure requirements with the available resources. As suggested by Nag[ 14], Figure 1 provides the steps that can be taken for cloud testing by an organization.
 | Figure 1 Cloud Testing Approach[ 14] |
(1)Explain Testing Strategy: It is the first step where organizations define their strategy for successful cloud testing. It includes objectives of testing, identifying the various types of testing, for example, system integration testing, user acceptance testing, performance testing, load testing, security testing. During this step, the testing environment is selected along with the timeline and risks like quality risks and inherited risks.
(2)Define Infrastructure Requirements: Infrastructure requirements for cloud testing is the second consideration in testing approach. It is based on an organization’s testing strategy. The infrastructure requirements may include hardware and software requirements, processing power, storage capacity, bandwidth, testing tools etc.
(3)Selection of a Service Provider: The selection of the service provider that can ensure e.g. reliability, quality, flexibility and productivity of services is a critical task. The organization can identify the service provider depending on the infrastructure requirements along with the testing tool licenses and provisioning. It is essential to have detailed insight on the types of services offered by the cloud provider in order to identify the most suitable service provisioning mechanisms.
(4)Start Testing: Organization can start their testing once the above mentioned steps are completed.
(5)Control and Measurement of Testing Goals: Monitoring and measurement is the final step which includes the validation of cloud testing on scheduled or event-driven basis. It helps organization to demonstrate the Return of Investment (ROI) of cloud testing.
Besides different challenges of the cloud testing approach, delivering testing in the cloud depends on the services that organizations are using. However, the main issue centers on the type of cloud used by cloud subscribers. Most of the cloud customers go with public clouds and the primary reason behind it is fast deployment, cheap CPU performance, low initial costs, easy integration with social media, and billing that is flexible and hourly[ 15].
Testing in public cloud environments presents different levels of responsibilities for security management depending on the services that are subscribed for by an organization. Services may include IaaS, PaaS, SaaS and HuaaS. Trusted third party cloud providers try to provide the best cloud security practices to cope with threats and risks according to the needs of different organizations.
In addition, providers need to support third-party audit and e-discovery initiatives depending on the circumstances of the organization. So, proper visibility should be maintained in the cloud. If data segmentation is not properly implemented in a public cloud, it may compromise the subscribers’ data confidentiality. Therefore the subscriber should understand the associated risks and threats for different cloud-based services.
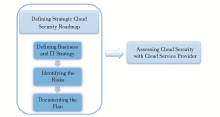
We propose an approach to secure the data as shown in Figure 2. After having started using the cloud testing approach, organizations could use this approach for better reliability and assurance on the security aspects.
(1)Defining Strategic Cloud Security Roadmap
There is not any ideal model that could define the fundamentals of security in the cloud as it depends upon the requirements of the organization. A cloud security strategy should include an evaluation of risks in the public cloud model. Third party cloud service providers should have various types of risk assessment methodologies to diminish the risks and threats. They should present their comprehensive frameworks of security to address the requirements of the organization.
①Defining Business and IT Strategy
It is an important step for a cloud provider and a customer organization to employ the security and define the business and IT strategy. In this step, both of them evaluate the following things to define their strategy:
·What is the information that is publicly accessed and needed to be stored or migrated to public clouds?
·What is the type of the organization and what could be the critical and confidential information from the viewpoint of the organization?
·What are the things that would be available and can be accessed by clients after migrating and testing on the cloud?
②Identifying the Risks
Cloud service providers help customer organizations to identify the threats, vulnerabilities and other risks based on the public cloud architecture. Providers help to design initial control mechanisms to diminish risks. They define the testing procedures according to the mechanism that helps to control ongoing risks or possible threats.
③Documenting the Plan
After defining test procedures and mechanisms, it is essential to document the entire plan. Identifying the types of workload and analyzing the requirements for security, legalization and regulations should be included in the plan. Cloud service provider works with the organization and makes a plan to control the risk with the help of identity and access management. The plan may also include ways to balance security controls between the organization and the cloud service provider.
(2)Assessing Cloud Security with the Provider
After developing a strategic cloud security roadmap, cloud service providers perform an assessment of the cloud security. The cloud service providers assess the current scenario of security in the organization with comparison to the organization’s objectives regarding security. During the assessment, they review the public cloud architecture from security viewpoint. It may include security policies and processes for accessing the data and its storage in an organization.
The assessment provides information about the remaining gaps in the current practices. This will disclose the strengths and weaknesses along with the vulnerabilities and possible threats to the organization. Such an assessment shows the possible ways of improvement and security measures that could remove gaps. The service provider can take additional steps by modifying existing security policies and procedures; by using additional security controls on the infrastructures and by implementing new controls for identity and access management.
Different studies have been done in the field of public cloud security. Below, we review existing literature discussing the security issues during testing in public clouds.
Trust in a public cloud environment can be defined as the level of customer’s certainty that the cloud provider is capable of providing the subscribed service properly and accurately. Organizations hand over to the cloud provider most of the security aspects which used to be under their direct control. So the subscriber should have a certain level of trust in the cloud provider. Figure 3 shows the level of trust boundaries in public cloud; this is relevant to testing as well. It explains that the trust between organizations and third party cloud providers depend upon the public cloud deployment model services like IaaS, PaaS, SaaS and HuaaS.
 | Figure 3 Public Cloud Trust Boundaries[ 16] |
As it can be seen from Figure 3, public clouds set the greatest challenge to security because of varying levels of trust boundaries. So, there should be trust in the data ownership and have a proper visibility in services and risk management between the provider and the customer. The concept regarding security measures in trust refers to the situation where all the possible risks are either removed or compressed to a minimum form[ 16].
In public cloud testing, there is a greater emphasize on the data than on the system. Therefore, it is necessary to govern and operate data and information by both subscribers and providers. While dealing with public clouds, governance refers to the management and control over policies, defining roles and responsibilities, standards for application development and special attention for managing risks[ 17]. In addition, governance also implies design, identification and implementation of organizational structures along with monitoring, control and testing of deployed services in the public cloud[ 18].
The minimal security processes and procedures set by an organization for acquiring computational resources can be easily bypassed leading to security vulnerabilities. Therefore, standard governance with the policies and procedures for security and privacy should be taken into consideration. So, organizations can assure reasonable security and can achieve proper flow of information with the cloud providers. Special tools and audit mechanism should be used to validate services; to ensure that risk has been managed; to know how the data has been manipulated and to verify the implementation of policies and procedures for security. Special types of programs like a risk management program should be implemented to control the upcoming unknown risks that have to be faced by the organization and the provider.
Compliance is also one of the security issues which are holding back companies from using public cloud services. According to a Gartner report “Compliance is the process of ensuring adherence to policies derived from internal directives, procedures and requirements, or from external laws, regulations, standards and agreements”[ 19]. So, compliance is the way of measuring the effectiveness and adherence of the rules and understanding the followed process.
The following types of questions could probably create an issue for compliance with international regulations[ 20]:
(1)Who will be responsible to assure that compliance has been met during testing in the public cloud - cloud provider or subscriber?
(2)Will the subscribers have information about the physical location of their data?
(3)Will the subscribers have access to log data from the public cloud to correlate it with events in other systems?
(4)Who will be accountable if someone frauds with the data from the subscriber’s public cloud in an attempt to disrupt systems in the subscriber’s internal data center?
(5)Who will be responsible if there is fissure of Personally Identifiable Information (PII)?
(6)Who will be responsible for the penetration test as it is the part of vulnerability management?
Moreover, cloud providers need to provide assurance and proof to the subscribers that they have control over security and the same applies to the subscribers also, as they need to verify with their own auditors. Most of the auditors are unaware about cloud computing and its services, which complicates the issue further. In addition, there are various types of security and privacy laws for handling and testing data within different countries. These kinds of issues make compliance a complicated security issue for public cloud testing.
In the cloud, increasing unauthorized access to the information is becoming a major concern[ 18]. So, Identity and Access Management (IAM) is a type of method which provides protection for the privacy and data sensitivity of information. Accrediting privileges to the users and providing usernames with login passwords are policies that can be managed by IAM. Moreover, IAM is a critical function for the organization and should be properly enforced to make authentication, authorization and auditing for testing of public cloud applications.
The challenges arising in IAM are considered as security issues during testing on public clouds[ 21]:
(1)Managing the identities results from the diversity of organization as they may be customers, staff, partners, employers etc.
(2)Diminishing the duplication of identities, characteristics and authorization.
(3)Manipulating the user’s identities during centralization and decentralization.
(4)Administrating the staff turnover in the organization.
The above mentioned challenges lead organizations towards the centralized and automated identity management system, which guides the identity federation. Therefore, centralized and automated identity management system is one of the solutions for the challenges, which can be achieved with the IAM standard protocols such as Security Assertion Markup Language (SAML), OAuth (Open Authentication), XACML (eXtensible Access Control Markup Language) and the OpenID Standard[ 18].
Availability concerns mainly the critical applications and data being available. It is a possible security issue in testing of public cloud applications. The effect may be temporary or permanent and the loss to the organization can be in fraction or full. Threats targeting availability can be either denial of service attacks, storage of resources or natural disasters[ 15].
(1)Interruption of Services
Cloud subscriber or provider has to face the interruption in service even though all the services and architectures are implemented properly for testing. The widely known incidents of cloud disruption include: Gmail had one-day outage in mid-October 2008, Amazon S3 had more than seven hour downtime on July 20, 2008 and similarly Flexi Scale had 18-hour outage on October 31, 2008[ 15, 22]. It is impossible to provide 100% availability and even at the level of 99.95% availability, 4.38 hours of disruption is expected in a year[ 15]. The enterprise users who require higher availability may take precautionary measures on-premises. For critical data, they can locate their backup inside their on-premises storage and for the applications; the users can keep on-premises versions of the applications. Even if the cloud service provider goes down, they can work offline and later on they can update with synchronization.
There may be permanent outages in the availability if the cloud service providers go out of business, incur a facility loss or bankruptcy. In 2009, the Federal Bureau of Investigation (FBI) raided at least two data centers in Texas due to complaints from AT&T and Verizon and after investigation the computing centers were permanently closed and this caused disruption in services to hundreds of businesses[ 23]. So, it is better to select viable providers and vendors with proper Service Level Agreements (SLAs) along with the redundancy links of different cloud providers.
(2)Distributed Denial of Services
Distributed Denial of Services (DDOS) is the attack where servers and networks are brought down by the flood of network traffic and prevent users to access the internet based services. Hackers and snipers are using botnets, which is the collection of compromised computers, to deny services which make it more difficult to troubleshoot this sort of attack. After all, popularity and publicity of the public cloud may also become a problem in the case of availability. The attackers target the place which is popular and the place from where they can get benefits. Similar things are happening to the public clouds. For example, the providers provide a registered mail address with valid passwords to give access to the required resources. If the user forgets the password, then he can recover it with some security questions. The attackers are snooping on the network for such activities[ 24]. This type of snooping may hamper the reliability of the public cloud computing during the testing phase also.
(3)Incompatibility
Incompatibility is one of the challenges during testing of public cloud applications. The storage services provided by one cloud vendor may not be compatible with the applications that need to be tested. So it would be better to choose compatible cloud vendor according to their testing criteria. For example the Simple Storage Service (S3) of Amazon is incompatible with Google, IBM’s Blue Cloud or Dell[ 25]. Therefore, it is better that the subscribers perform testing with the same cloud vendor that is hosting their (subscriber’s) online applications and infrastructures.
Public clouds use multi-tenant environments, so that the data from different users will be stored in the shared environment. Therefore data protection and its confidentiality are also critical issues and key concerns for the vendors which may lead to fraud and financial extortion. Data protection and its security are not only concerned with confidentiality, sometimes they are also concerned with judicial issues. The service providers need to provide assurance to the customer organization that only authorized users have access to the data when in transit, at rest and in use. Access control and Encryption are measures for the data security. For reliable protection of data, the cloud service providers should set the goals on the following points[ 26]:
(1)Assure users that their data has been stored properly and can be retrieved when needed.
(2)Effective search of the malfunctioning server when the data corruption is detected.
(3)Ensure data protection even if the users modify, delete or add.
(4)Minimize the effect on data that has been caused by the system failures or data error.
(5)Allow users to check the status of their data with minimum deprivation.
Therefore in data security, feasible access control of data with confidentiality would be done by encrypting data and providing decryption key only to authorized persons of the organization. This has been considered as a valid method and is widely acknowledged by cloud providers and subscribers for having secure data storage on untrustworthy servers. Data sanitization is another good measure for data security. It is the process of removing sensitive data from a storage device in various situations[ 27].
Instance isolation is the procedure of ensuring that different instances running on the same physical machine are detached from each other[ 27]. It is possible to get flexible and reliable services in an economical way after having multi-tenancy over a large number of platforms. This could be achieved through the concept of isolation and flexible delivery of the services from the cloud providers. The hypervisor splits physical servers into number of instances, each with their own Operating System (OS), allowing even small customers and guest users to access the public cloud for testing. It allows one virtual machine user to gain access to the data of another virtual machine user, which possibly brings new threats and risks. The suspect can steal user’s information by logging unknowingly and spread malware in the architecture of the public cloud. For example, in 2009, attackers destroyed the data of 100,000 websites. The attackers were able to get access to the servers by exploiting a critical vulnerability in HyperVM (Hyper Virtual Machine) made by a company called LXLabs[ 28]. So when hypervisor is introduced to gain new capabilities, it adds new risks and potential for exploitation. Even though, it is a benefit of the public cloud, it would be difficult for the existing customers as they remain susceptible to attacks.
The alternative solution has been developed to patch up this hypervisor vulnerabilities. NC State and IBM researchers have come out with the prototype security tool which runs outside the hypervisor to determine the hypervisor’s security and the tool is termed as Hyper Sentry software[ 29].
A public cloud is based on a multi-tenanted environment and the architecture built on it increases complexity. A public cloud enables a decoupling of the layers and it enables one vendor’s SaaS to be hosted within some other vendor’s PaaS, or IaaS service. Therefore, this type of nested hosting arrangement of the architecture has platform and network risks which may bring a lack of transparency between the customers and actual point of operations even during testing[ 30].
Hypervisor can bring challenging issues in architecture too. It is an additional layer of software between OS and hardware platform. It also helps the public cloud vendor and user in launching and terminating the instances of the Virtual Machine (VM). But such features bring complexity in the architecture of public clouds and it would increase the attack over surface of the cloud. In addition, most of the virtual machines on the same host have the capability to create software based switches and network configurations for efficient and direct communication. However this could bring loss of visibility and protection in the architecture of the public cloud. Client-side protection and server-side protection are also essential to have a secure architecture in the public cloud. For the overall security in the architecture, it is better to have secure client-side before testing the public application and review the existing measures and upgrade if required. Backdoor Trojan, keystroke logger or any types of malware running on the client side could be an issue, so it is better to take precaution on it.
The security threats appear in all shapes and sizes. According to the security issues that would arise during testing of public cloud applications, the possible threats posed by four service models are listed in Table 1[ 11, 16].
| Table 1 Top Threats in Different Service Levels |
The European Network and Information Security Agency (ENISA) risk assessment process proposed in November 2009 along with Gartner’s risk assessment for security analyzed the aforementioned security issues[ 31]. During the risk assessment of security issues, the following points were considered:
Analyzing the risks based on the on-premises data along with cloud based storage data of the cloud subscriber that will be in use during testing.
The level of risk will be different on the basis of cloud architecture.
The risk assessment applies to testing of public cloud applications. The assessment presented here doesn’t replace any organization’s own risk assessment.
The level of risk has been inspected from the viewpoint of both cloud provider and subscriber.
Four different levels of risk have been proposed as Low, Medium, High and Very High. The risk level is the function of business impact and the incident scenario with its response. The estimation of the risk level is based on ISO/IEC 27005:2008.gives the detailed view of the risk assessment on eight security issues. It shows the risk levels with their probability of occurrence and impact over the assets of public cloud customers and providers during testing of public cloud applications.
| Table 2 Risk Assessment of Eight Security Issues |
Lots of work has been done discussing different service providers from academic or enterprise perspectives. However there is the lack of information of public cloud service providers in terms of security during testing. The diversity of the public cloud providers raises questions among potential subscribers about the providers’ abilities to meet the subscribers’ requirements. Therefore, third party public cloud providers should consequentially consider the risks and threats related to security issues so as to assure and gain confidence from customers.
We performed an empirical survey to gather information on four popular public cloud providers: Amazon Web Services (AWS), Microsoft Azure, Google App Engine (GAE) and Rackspace Cloud Servers. Amazon AWS and Rackspace Servers are the top two cloud providers who are hosting more than 350,000 websites in internet through their cloud platform[ 32]. Google App Engine is a unique PaaS provider in the public cloud and Microsoft Azure is a new competitor in the market. Microsoft Azure offers similar services as AWS in computation and storage services. We selected these providers due to their popularity and were interested in finding out more about them on the basis of the eight security issues presented in section 4.
In the survey we investigated the strategies of public cloud providers on handling security issues and threats as viewed by different potential public cloud users. The survey yielded 32 (N=32) full responses from different companies. Even though the responses were few in numbers, this survey provides some useful information about the strategies of public cloud providers. One of the main problems during the data collection process was how to find the appropriate sample of the public cloud users and potential users of testing. Therefore, sending email invitations for the survey and using certain online social networking forums were chosen as the most efficient ways to identify the targeted respondents. On the basis of eight security issues, the survey questionnaire was designed to collect information from the cloud service subscribers.
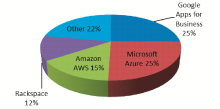
The status quo of public cloud providers shows that the percentage of customers using Google Apps for Business and Microsoft Azure is higher compared to the remaining public cloud providers even though some of them have been providing cloud services for a longer period of time. 25% of the customers are using Google Apps for Business and 25% of the customers are using Microsoft Azure as shown in Figure 4. The possible reasons for the high proportion are the brand names of the companies and new concepts of security strategies implemented by Google and Microsoft in the marketplace.
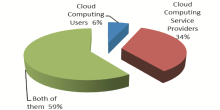
The survey revealed that 59% of the customers think that both the cloud provider and the subscriber must be responsible for proper implementation of security as shown in Figure 5.
of public cloud applications during testing?
The data from individual respondents was collected using the Likert scale (Very Strong = 4, Strong = 3, Satisfied = 2 and Dissatisfied = 1). Using the data we drew the following conclusions as shown in Table 3:
| Table 3 Comparing Strategy of Popular Public Cloud Providers |
Trust and data protection seem to be the two security issues that have been properly addressed by public cloud service providers, but there is still a lack in addressing issues related to governance. The public cloud subscribers expressed high concerns for trust and data security during testing. The risk assessment of eight security issues in Table 2 yielded that the risk factor is high for trust, governance, compliance, instance isolation and its failure, data security and architecture. However, most of the public cloud providers are not addressing some of the security issues as high risk factors. Therefore, there is a need to build appropriate approaches for security issues having the high risk.
The use of cloud computing enables organizations to focus on their core objectives, rather than worry about their infrastructure. It offers similar opportunities for testing public cloud applications. As companies place their information in the cloud, there are concerns about the security and safety of the information. Providing cloud services with high-assurance of security has become an elusive goal of public cloud service providers. Therefore in this study, we identified security issues, risks and threats which may occur during testing of public cloud applications. Risk assessments of security issues help in concluding how secure it is to perform testing of applications in public cloud platforms.
The literature review evaluated eight security issues to estimate the level of risk. The assessment performed by ENISA as presented in section 6 shows that every issue is crucial as six security issues have high risk factors. Threats are interrelated with the security issues as threats come in different dimensions. Different types of threats in different levels of services are unpredictable, so it is better to follow proper guiding principles to adopt and extend security tools of public cloud service provider to provide end-to-end trustworthy services to the customers. The impacts over the assets of public cloud customers and providers caused by security issues and threats also help to determine the level of risk during testing on public cloud.
It seems to be insecure to do testing of an application in the public cloud environments, if there is lack of proper exercise in risk management. Risk management results in assessing and identifying risks and therefore helps to reduce the risks. It is challenging to assess and identify the risk in every service level of cloud during testing. During the entire system lifecycle from design to testing, risks that have been diagnosed should be carefully balanced with the available means of security. In addition, the testing teams should equip themselves with the security strategy to test the applications in the cloud environment with smaller probability of risk.
The survey concerning the four popular public cloud providers shows that every provider is well conscious about the security issues, privacy and threats. Different security strategies have been implemented under the guidance of federal agencies. The study done on public cloud providers also demonstrated that the service providers are struggling to provide their best security strategies to customer organizations. The survey suggests that public cloud providers have a good potential to offer testing on public cloud environments with trust, availability, data security, secure authentication and compliance. On the other hand, it also shows the exposure to threats due to problems in governance, control and audit mechanism.
Overall, both the cloud providers and subscribers should ensure that security and privacy controls are implemented correctly and operated as intended. Federal agencies like NIST should play significant roles and ensure that all the public cloud service providers meet the required criteria of security and privacy. Public policy and jurisdictional issues should be solved by federal agencies in order to achieve secure cloud computing and testing. Therefore, it is advisable to have a background study of different public cloud service providers before testing applications in public cloud environments. For all the risks, a proper mutual understanding between the public cloud service provider and the subscriber can give a good output.
| [1] |
|
| [2] |
|
| [3] |
|
| [4] |
|
| [5] |
|
| [6] |
|
| [7] |
|
| [8] |
|
| [9] |
|
| [10] |
|
| [11] |
|
| [12] |
|
| [13] |
|
| [14] |
|
| [15] |
|
| [16] |
|
| [17] |
|
| [18] |
|
| [19] |
|
| [20] |
|
| [21] |
|
| [22] |
|
| [23] |
|
| [24] |
|
| [25] |
|
| [26] |
|
| [27] |
|
| [28] |
|
| [29] |
|
| [30] |
|
| [31] |
|
| [32] |
|